Listing AD Users with PowerShell

Full-Access Members Only
Sorry, this lesson is only available to Server Academy Full-Access members. Become a Full-Access member now and get instant access to this and many more premium courses. Click the button below and get instant access now.
Instructions
Q&A (0)
Notes (0)
Resources (0)

Saving Progress...
Resources
There are no resources for this lesson.
Notes can be saved and accessed anywhere in the course. They also double as bookmarks so you can quickly review important lesson material.
In this lecture, we are going to be learning how to list Active Directory users with Windows PowerShell.
I am logged into a server that has Active Directory installed. This is the IPDC01 server.
NOTE: If you don’t have an Active Directory you will not be able to follow along in this lecture.
Let’s start by opening PowerShell. Click on the Windows icon on the bottom left and type powershell. I am going to select Windows PowerShell ISE.
Now, the first thing we are going to do is write a comment. Press Shift+3.
This # preceding the line is a comment, and will not get executed by PowerShell.
Next, we type Import-Module ActiveDirectory.
NOTE: When we type a command in the editor it gets populated by the Intellisense feature.
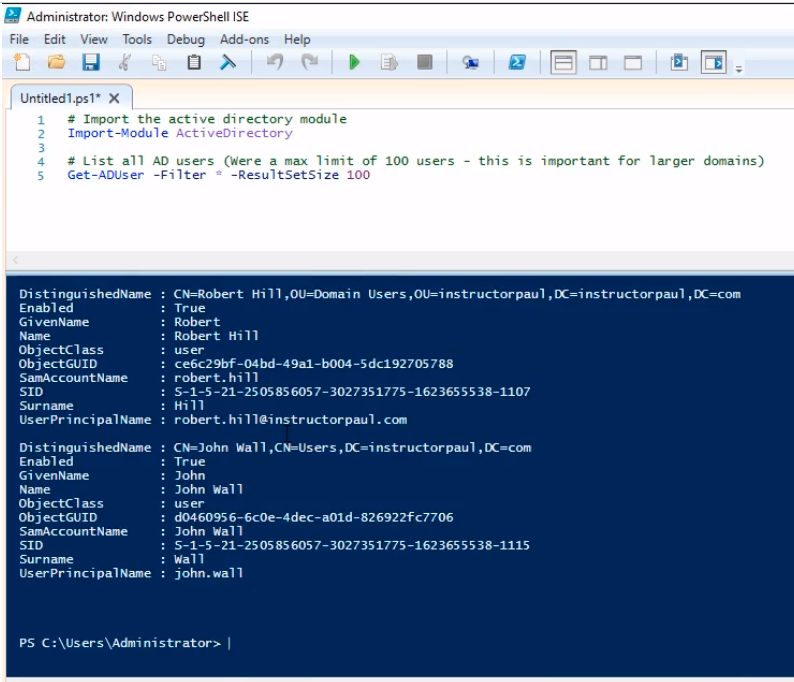
Let’s continue writing the code. The script will look as follows:
# Import the active directory module
Import-Module ActiveDirectory
# List all AD users (Were a max limit of 100 users - this is important for larger domains)
Get-ADUser -Filter * -ResultSetSize 100
Press the green Play button at the top to execute the script.
We see the results at the bottom pane of Windows PowerShell ISE.
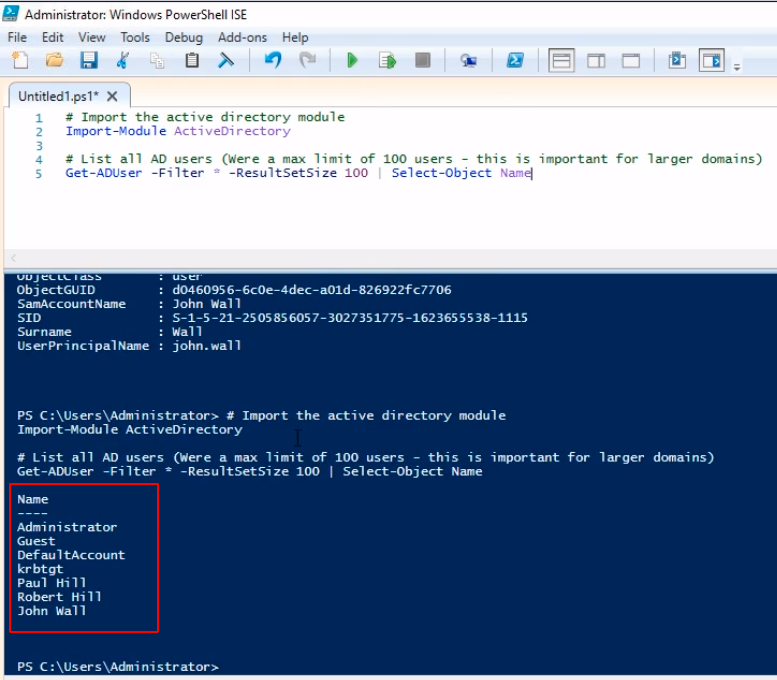
Let’s try another example. Let’s do a list that is more user-friendly. Type the following code:
# Import the active directory module
Import-Module ActiveDirectory
# List all AD users (Were a max limit of 100 users - this is important for larger domains)
Get-ADUser -Filter * -ResultSetSize 100 | Select-Object Name
Press the green Play button at the top to execute the script.
We get now a list that is a lot easier to read.
We can also select multiple objects. If we want to select UserPrincipalName we can add it next to the Name at the end.
# Import the active directory module
Import-Module ActiveDirectory
# List all AD users (Were a max limit of 100 users - this is important for larger domains)
Get-ADUser -Filter * -ResultSetSize 100 | Select-Object Name, UserPrincipalName
Press the green Play button at the top to execute the script.
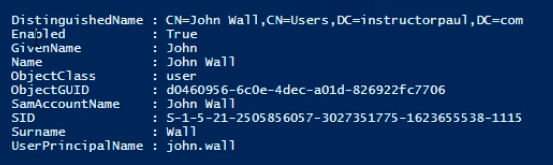
We now get a list with the UserPrincipalName.
Some are not populated, and that's fine.
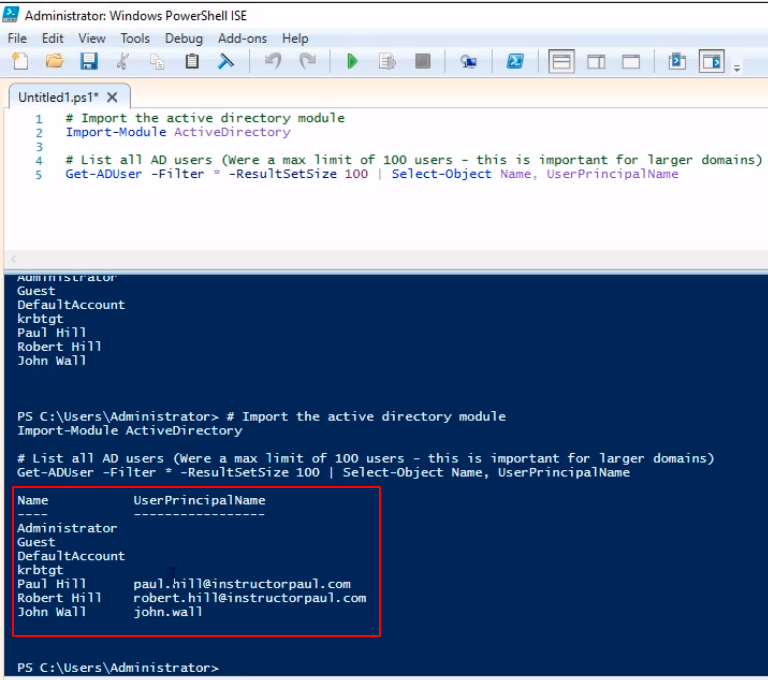
We can also choose other field values from the complete first output like Surname, where is Enabled or not, etc.
So, if I type in:
# Import the active directory module
Import-Module ActiveDirectory
# List all AD users (Were a max limit of 100 users - this is important for larger domains)
Get-ADUser -Filter * -ResultSetSize 100 | Select-Object Name, Enabled
We should get the following output:
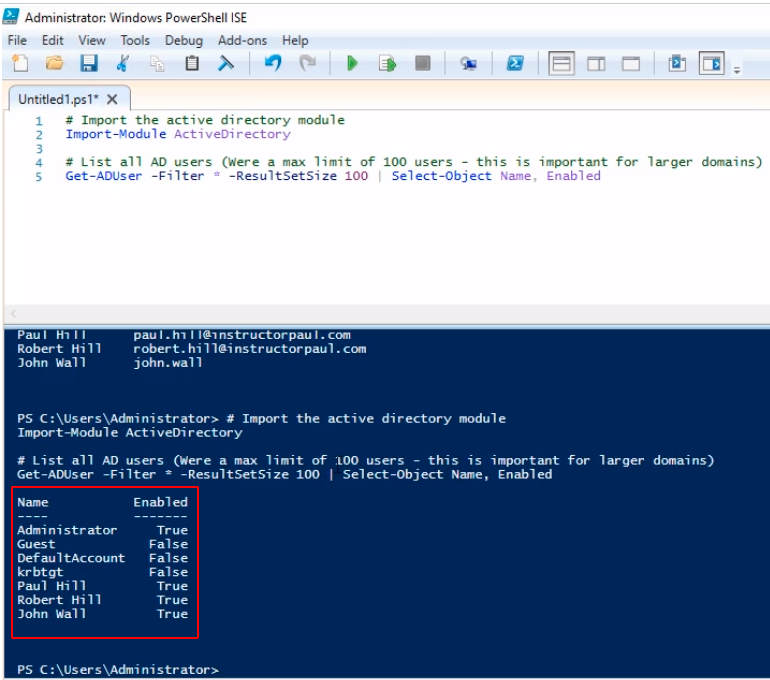
We can select different properties, so if we want to see the last logon we can do the following:
# Import the active directory module
Import-Module ActiveDirectory
# List all AD users (Were a max limit of 100 users - this is important for larger domains)
Get-ADUser -Filter * -ResultSetSize 100 -Properties lastLogon | Select-Object Name, Enabled, lastLogon
The result will be the following:
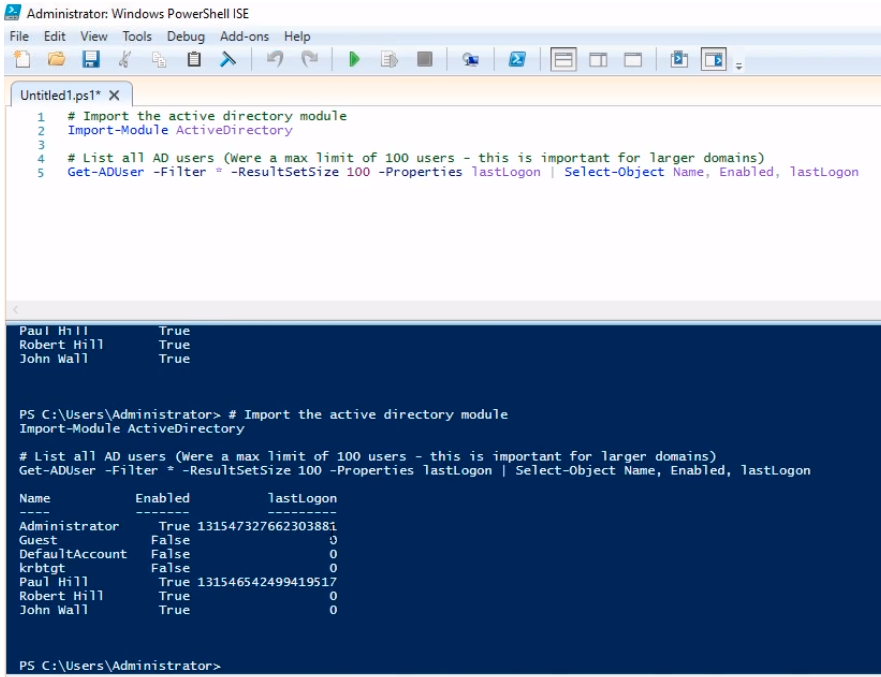
The lastLogon is an LDAP timestamp, and is not human-readable. The timestamp is the number of 100-nanosecond intervals (1 nanosecond = one billionth of a second) since Jan 1, 1601 UTC.
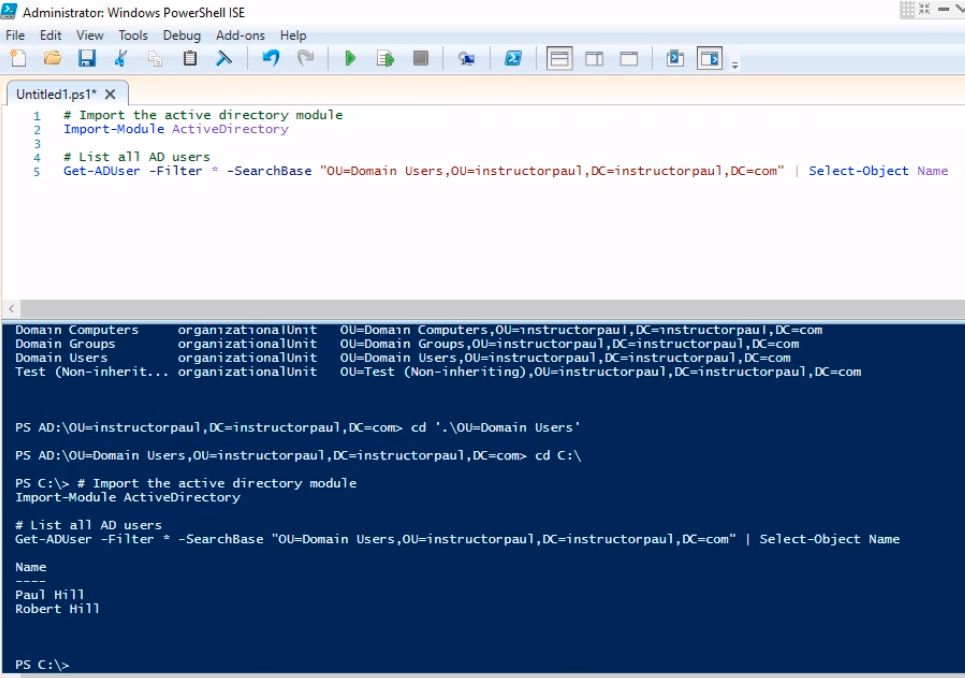
Now, let’s take a scenario where we want to list all the user accounts inside an Active Directory OU. The way we would do that is under Get-ADUser we would do the following using SearBase. We will enter the Distinguished Name of the OU that we are looking for.
# Import the active directory module
Import-Module ActiveDirectory
# List all AD users inside a OU
Get-ADUser -Filter * -SearchBase "OU=Domain Users,OU=instructorpaul,DC=instructorpaul,DC=com" | Select-Object Name
Now, let’s take a scenario where we want to list all the members from a Security Group. We will use the Roaming Profile Users group.

Server Academy Members Only
Sorry, this lesson is only available to Server Academy Full Access members. Become a Full-Access Member now and you’ll get instant access to all of our courses.



Good lesson, Thank you 👍
i can’t cd into AD
Hi ALWI DELGADO ALAUDIN
ALWI DELGADO ALAUDIN
Can you provide more information about it?
Ricardo
Where did Paul’s Roaming Profile User OU come from? I don’t have that in my ADUC
Hi dinman68
dinman68
It might have been there from a previous lesson. I suppose Paul used it because he knew there was a user, but you can use any other Security Group that has users, or add one Security Group and add a User.
-Ricardo