Configuring S3 permissions and access controls

Server Academy Members Only
Sorry, this lesson is only available to Server Academy members. Create a free account now to get instant access to this and more free courses. Click the Sign Up Free button below to get access to our free courses now, or sign in if you have an account.
Instructions
Q&A (0)
Notes (0)
Resources (0)

Saving Progress...
Resources
There are no resources for this lesson.
Notes can be saved and accessed anywhere in the course. They also double as bookmarks so you can quickly review important lesson material.
It's important to ensure that only authorized users have access to your data. S3 allows you to set fine-grained permissions on individual objects and buckets, so you can control who can access your data and what actions they can perform. By default, all S3 resources (buckets and objects) are private. Meaning only the resource owner can access them.
The resource owner can give access to others through resource-based policies (attached to the resource) or user policies (or identity-based policies). Access control lists (ACLs) can also be used to grant basic read and write permissions to other AWS accounts. However, it is generally recommended to use policies rather than ACLs for access control.
Identity-based Policies
Identity-based policies are policies that are attached to an identity (IAM user, group, or role). These policies specify the permissions that the identity has, such as the actions they can perform and the resources they can access. Identity-based policies can be managed (saved and managed in IAM) or inline (included directly in the identity's JSON policy document).
You will learn more about identity-based policies in our IAM section so this course will focus on resource-based policies.
Resource-based Policies
Resource-based policies are policies that are attached to a resource (or an S3 object in this example) and specify who has access to the resource and what actions they can perform on it. These policies are inline only, meaning that they are defined directly within the resource's configuration and cannot be managed independently from the resource. Resource-based policies can be used to grant permissions to other AWS accounts or IAM users, groups, and roles within your account
Configuring Bucket Policies
To configure an S3 Bucket Policy, open the S3 Buckets dashboard then select the desired policy (in my case, myfirstbucket129).
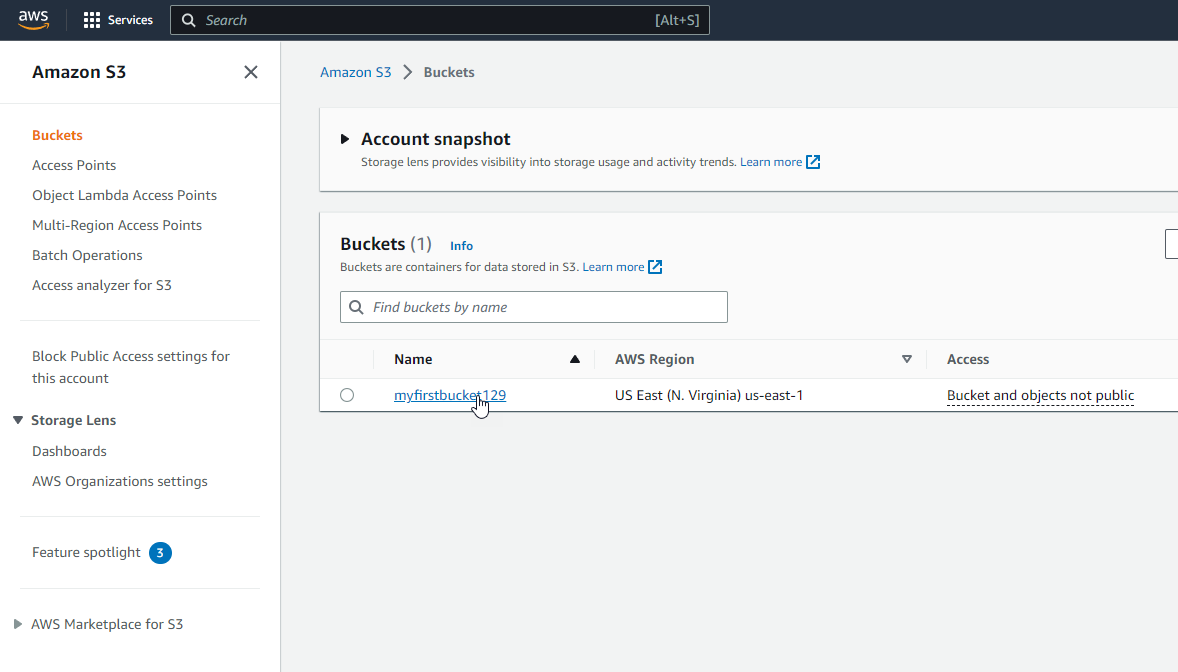
Next, click the Permissions tab:
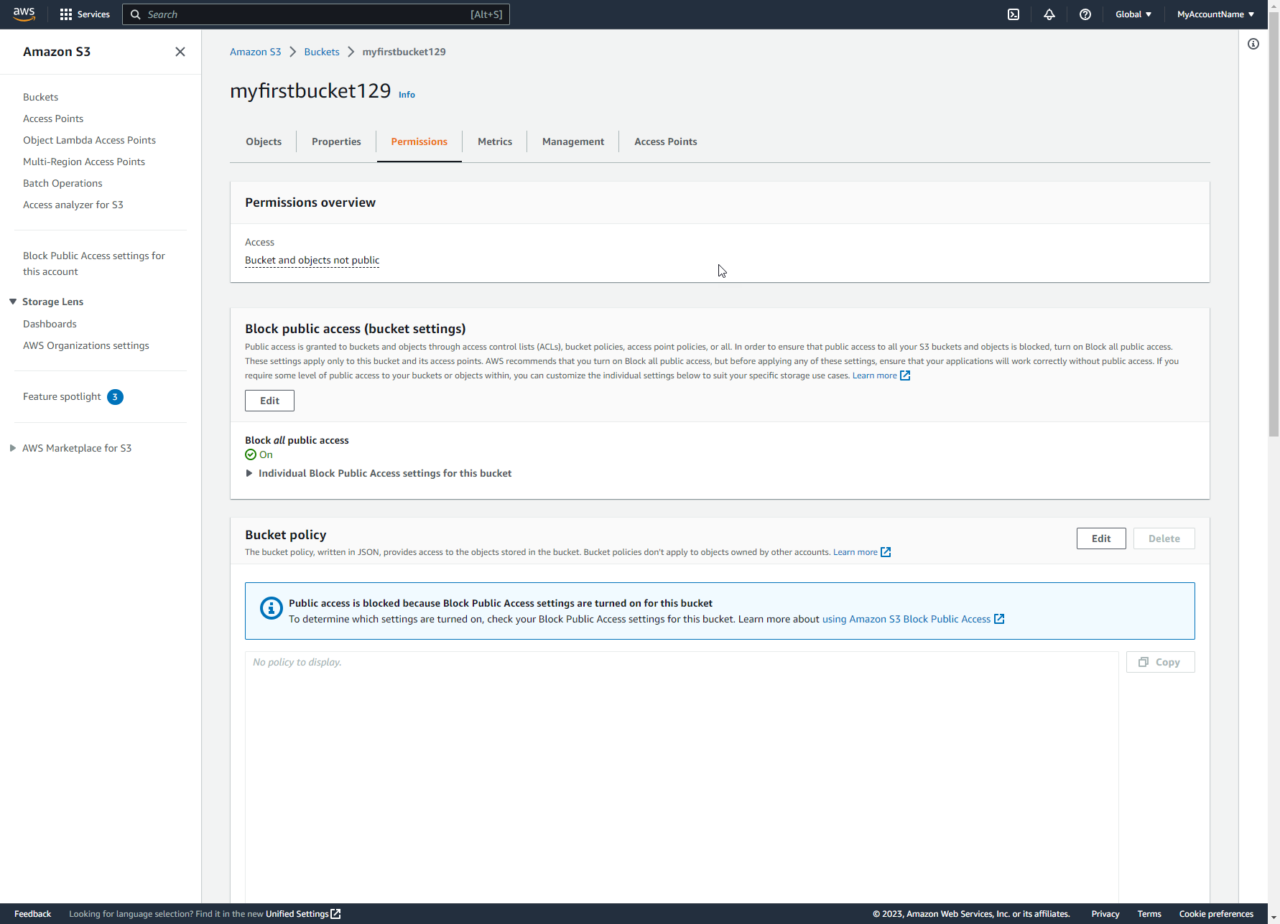
This page allows us to enable or disable public access:
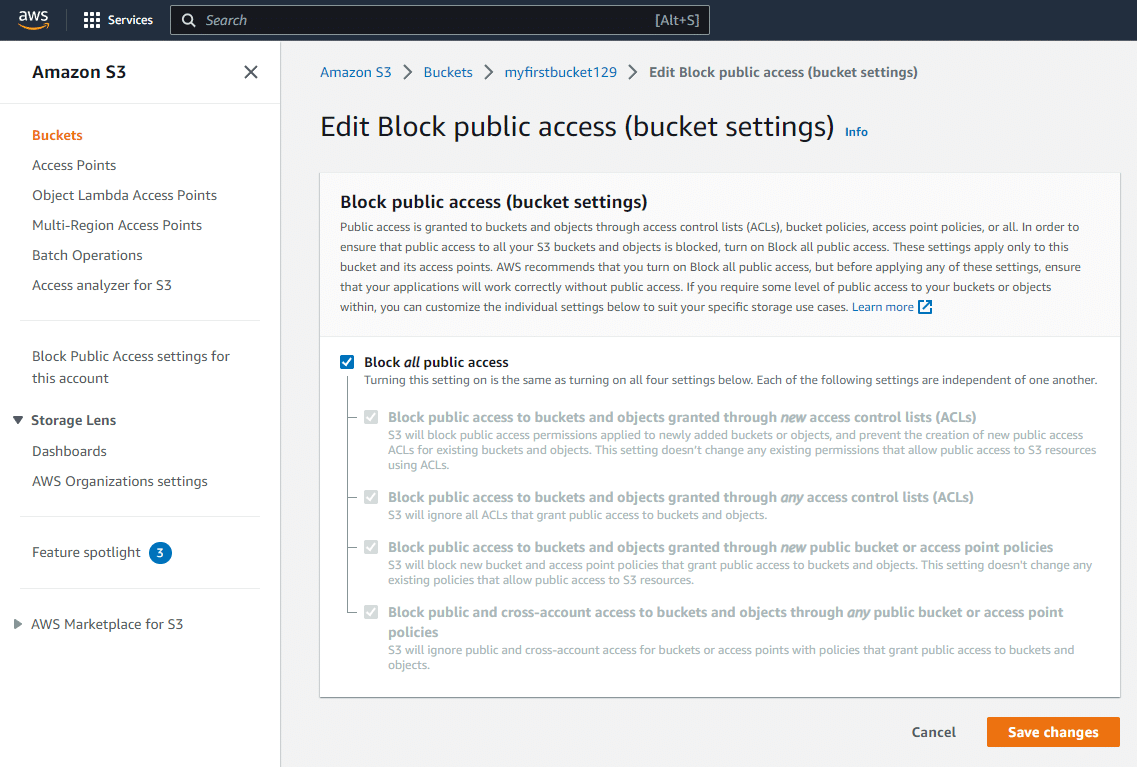
If you want to enable public access to your S3 bucket, you can uncheck the Block all public access checkbox and click Save changes.
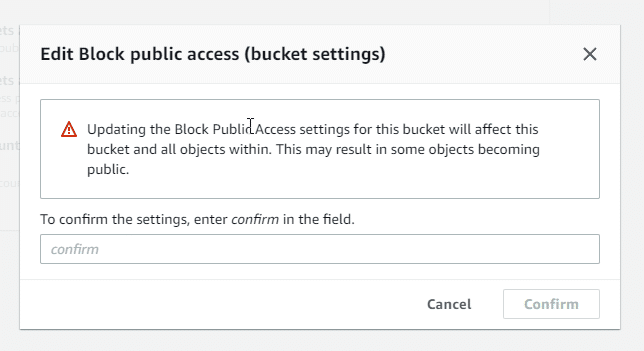
This does not mean that all objects are public. Instead, it makes it possible for some S3 objects to be set to public. If you wanted to make our aws.zip file public, we still cannot because of the bucket owner enforced setting setting is applied for Object Ownership:
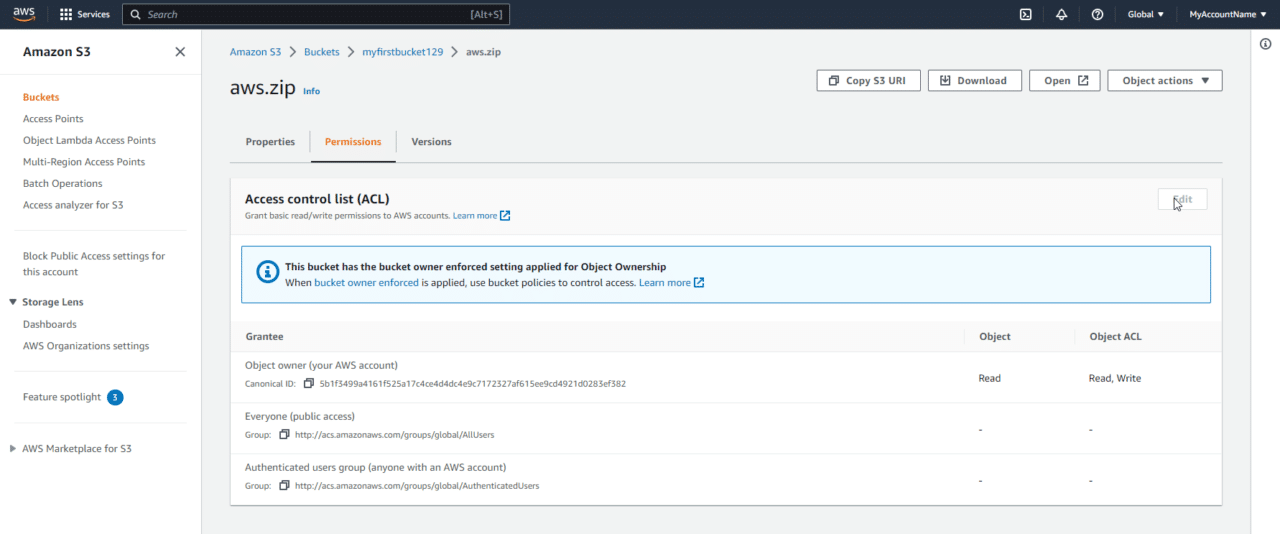
Enable Object ACLs for Object Ownership
To change this, on the S3 Bucket permissions tab, scroll down to the Object Ownership section. Click Edit:
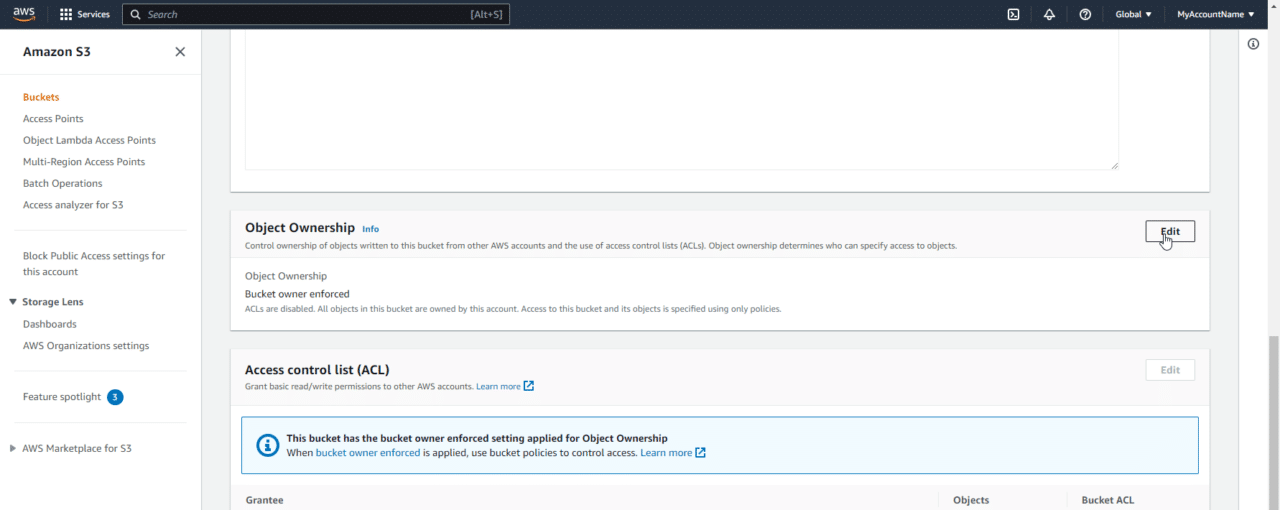
Next, we can enable ACLs and acknowledge that ACLs will be restored. Click Save changes.
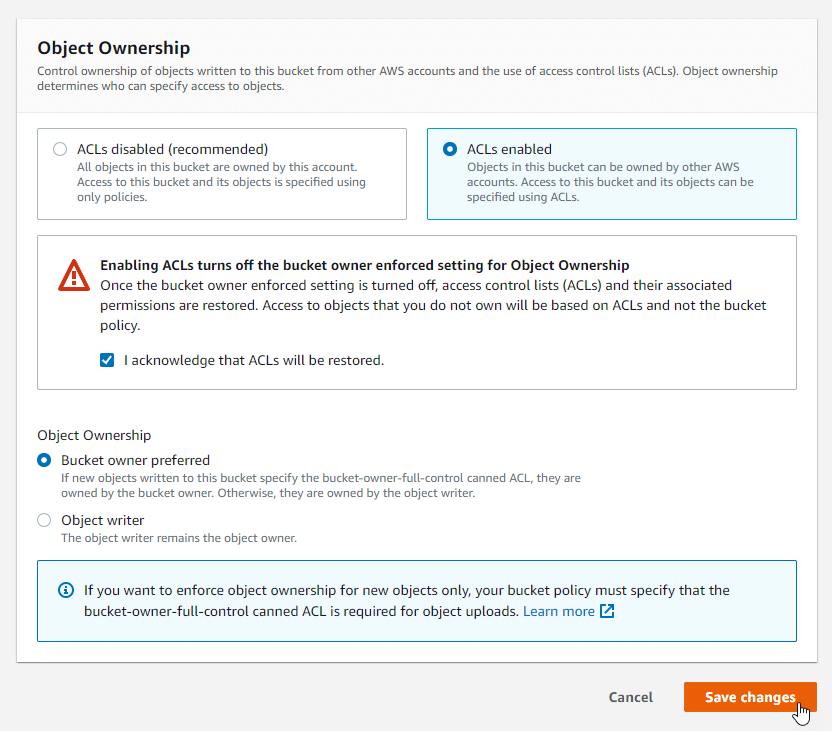
Configuring Object ACLs
Now we can scroll down to the permissions section and grant Read permissions to Everyone by clicking the Edit button:
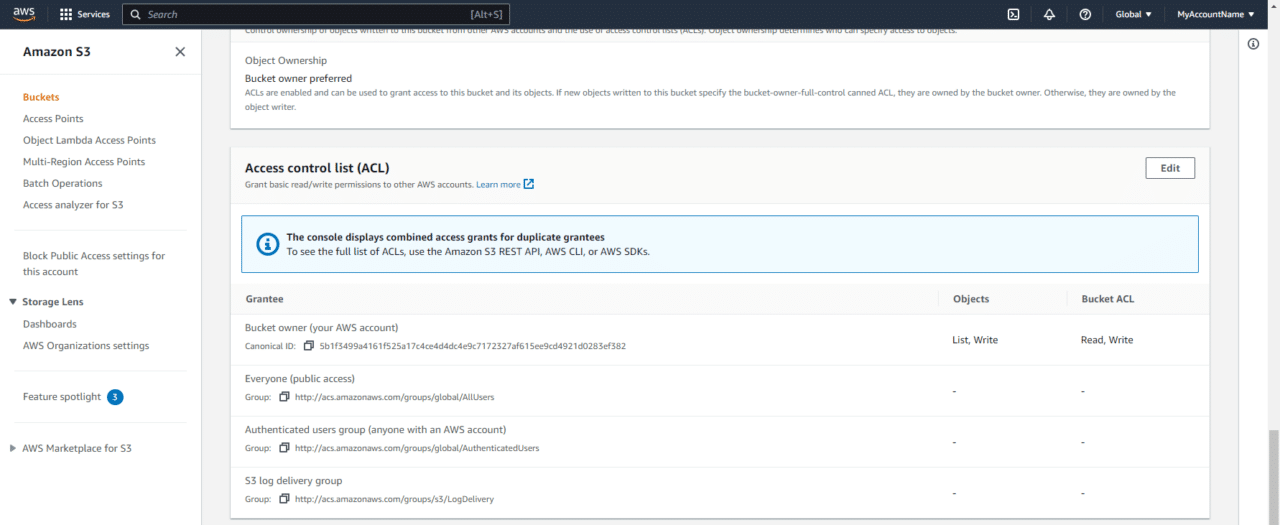
Before we make any changes, you will notice for the grantee Everyone there is list and read for Objects and Object ACL:
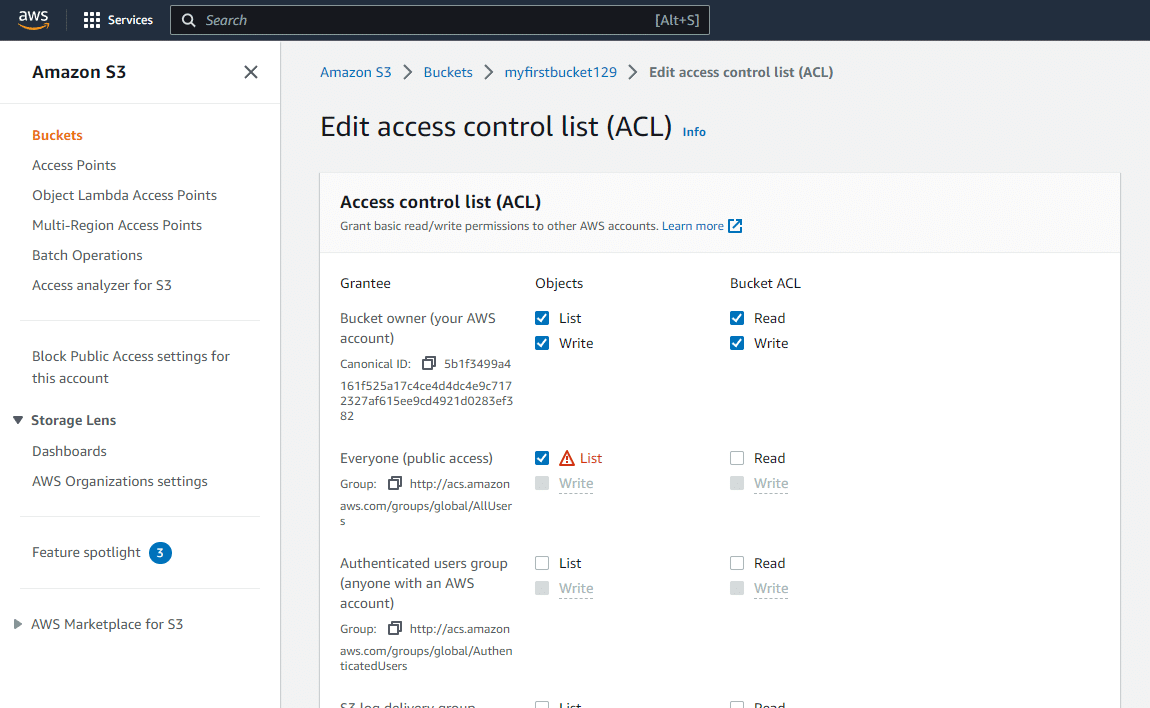
Let's explain the difference between these two:
- Objects
This controls the grantee's (in this case, everyone's) access to the individual object. This will allow the object to be downloaded by everyone.
- Object ACL
This controls access to view or write to the specific Object ACL, which we would never want everyone to write to (which is why it isn't possible to select).
Add Read permissions to the ACL:
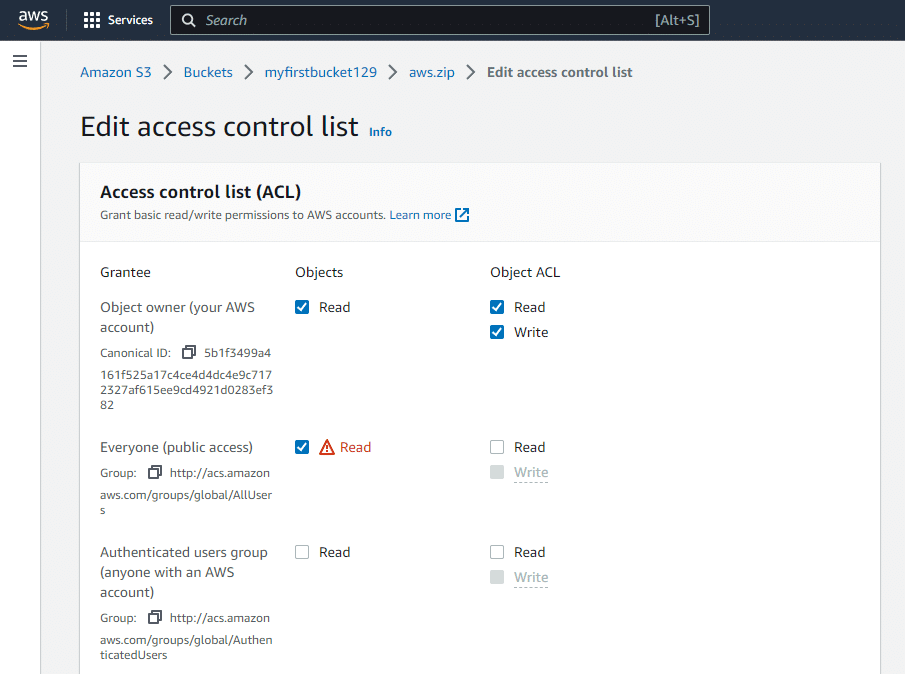
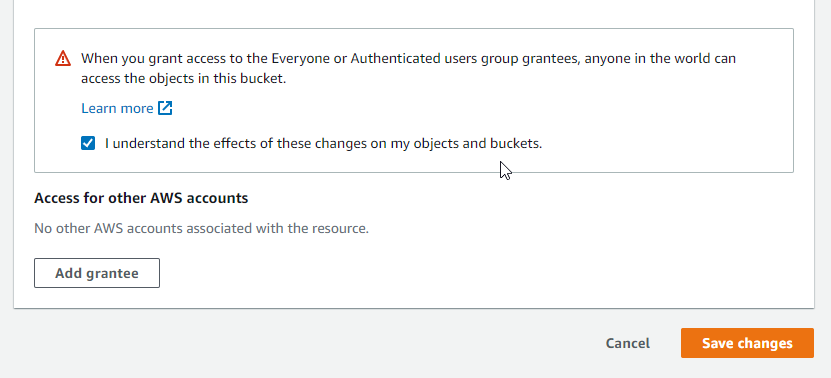
At the bottom you'll need to confirm that you want to grant access. Click the checkbox, then select Save changes:

Server Academy Members Only
Want to access this lesson? Just sign up for a free Server Academy account and you'll be on your way. Already have an account? Click the Sign Up Free button to get started..



Hello,
I am much interrested to ACLs for S3.
Is it possible to provide any course using JSON?
I didn’t check yet if there is a training of that in serveraccademy but it should be interresting to have that knowledge if we I ought to to use that tools.
Thank you!
Hi André Serville
André Serville
Thank you for your suggestions. I’ll ping Paul Hill so he can see your post.
Paul Hill so he can see your post.
I agree that it is important to have knowledge of JSON formats. Most of the JSON code is somewhat understandable in many cases but I see your point that it needs to be explained when it comes to S3.
Ricardo
Regarding the following code you posted in the review:
{
“Version”: “2012-10-17”,
“Id”: “ExamplePolicy01”,
“Statement”: [
{
“Sid”: “ExampleStatement01”,
“Effect”: “Allow”,
“Principal”: {
“AWS”: “arn:aws:iam::123456789012:user/Dave”
},
“Action”: [
“s3:GetObject”,
“s3:GetBucketLocation”,
“s3:ListBucket”
],
“Resource”: [
“arn:aws:s3:::awsexamplebucket1/*”,
“arn:aws:s3:::awsexamplebucket1”
]
}
]
}
Version: Specifies the version of the policy language being used. In this case, it’s “2012-10-17,” which refers to the version of the policy language.
Id: An optional identifier for the policy. This can be any unique string that helps you identify the policy.
Statement: This is an array of individual policy statements. In your JSON, there is a single statement defined.
Sid: The Statement ID is an optional identifier for the individual statement. It can be useful for tracking and managing statements.
Effect: This determines whether the permissions specified in the statement are allowed or denied. In this case, it’s set to “Allow,” indicating that the permissions are granted.
Principal: Specifies the AWS entities that are affected by the policy. In this case, it’s an IAM user with the ARN (Amazon Resource Name) “arn:aws:iam::123456789012:user/Dave.”
Action: Lists the AWS actions (API operations) that the user is allowed to perform. The actions listed are:
s3:GetObject
s3:GetBucketLocation
s3:ListBucket
Resource: Lists the Amazon S3 resources to which the permissions apply. In this case, the resources are specified using their ARNs:
“arn:aws:s3:::awsexamplebucket1/*” – This allows the user to perform the specified actions on objects within the bucket.
“arn:aws:s3:::awsexamplebucket1” – This allows the user to perform the specified actions on the bucket itself.
I hope it helps clarify and explain these lines of JSON code.