Analyzing Dropped Traffic Logs in Linux

Full-Access Members Only
Sorry, this lesson is only available to Server Academy Full-Access members. Become a Full-Access member now and get instant access to this and many more premium courses. Click the button below and get instant access now.
Instructions
Q&A (0)
Notes (0)
Resources (0)

Saving Progress...
Resources
There are no resources for this lesson.
Notes can be saved and accessed anywhere in the course. They also double as bookmarks so you can quickly review important lesson material.
In this lesson, you will learn how to configure logging for dropped traffic with iptables. We'll start by installing the nginx package, which is an easy web server which only requires one command to start, then you'll configure your logging rules, next you'll generate traffic that will get blocked be iptables, then we'll allow the traffic in iptables so you can access the nginx web server from your host computer.
Step 1: Configure logging (if you haven't already)
In the best practices lesson, we briefly mentioned that you should be logging all dropped traffic. You can quickly tell if iptables is configured to log by running the iptables -L command and looking for an entry like so on bot INPUT AND OUTPUT chains:
target prot opt source destination
LOG all -- anywhere anywhere limit: avg 10/min burst 5 LOG level warning prefix "iptables INPUT dropped: "If you don't see output like that, you can add those rules here:
sudo iptables -A INPUT -m limit --limit 10/min -j LOG --log-prefix "iptables INPUT dropped: "
sudo iptables -A FORWARD -m limit --limit 10/min -j LOG --log-prefix "iptables FORWARD
dropped: "
sudo iptables -A OUTPUT -m limit --limit 10/min -j LOG --log-prefix "iptables OUTPUT: "Step 2: Installing Nginx on Ubuntu Server
First, install Nginx on your Ubuntu Server VM. Nginx is a popular web server that can serve web pages to clients.
# Install NGINX
sudo apt install nginx
# Configure to start automatically on boot
sudo systemctl enable nginx
sudo systemctl start nginxAfter the installation, ensure that Nginx is running:
systemctl status nginxBefore we move on to the next steps which will be completed on our host computer, let's start tailing our iptables logs which (on Ubuntu), will be located in /var/log/syslog:
sudo tail -f /var/log/syslog | grep 'iptables'Leave that command running while you continue on to the next step.
Step 3: Attempt to accessing the default Nginx page
On your host computer, open a web browser and navigate to the IP address of your Ubuntu VM. For me, my VMs IP is 192.168.1.153, so I will navigate to http://192.168.1.153. This should eventually timeout:
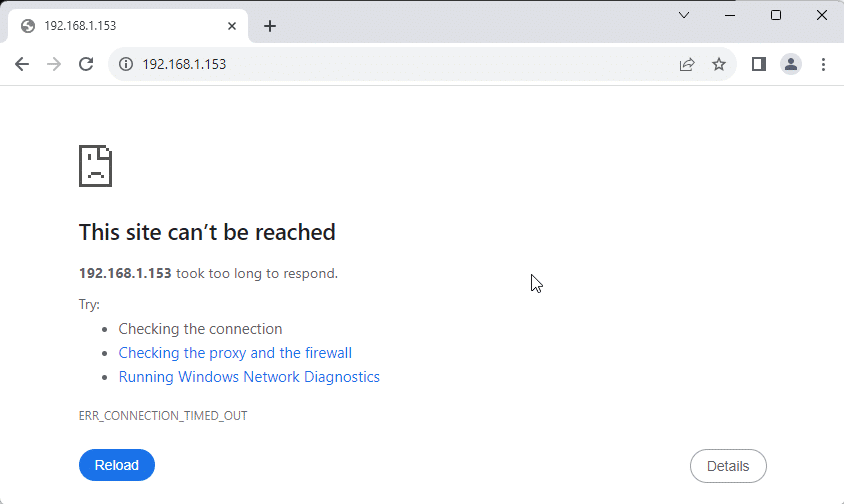
Back on our Linux server, we should show several attempts to access the server on port 80 that are being dropped:
Nov 26 16:15:40 ubuntu-server kernel: [ 559.743238] iptables INPUT dropped: IN=enp0s3 OUT= MAC=08:00:27:3e:6b:88:78:2b:46:c8:7f:94:08:00 SRC=192.168.1.156 DST=192.168.1.153 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=51981 DF PROTO=TCP SPT=54536 DPT=80 WINDOW=64240 RES=0x00 SYN URGP=0
Nov 26 16:15:48 ubuntu-server kernel: [ 567.743527] iptables INPUT dropped: IN=enp0s3 OUT= MAC=08:00:27:3e:6b:88:78:2b:46:c8:7f:94:08:00 SRC=192.168.1.156 DST=192.168.1.153 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=51985 DF PROTO=TCP SPT=54536 DPT=80 WINDOW=64240 RES=0x00 SYN URGP=0Step 4: Allow Access to Port 80
Before we add a new rule to allow port 80, we should list all of our iptables
sudo iptables -L --line-numberMy input chain shows the following:
Chain INPUT (policy DROP)
num target prot opt source destination
1 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh
2 ACCEPT all -- anywhere anywhere
3 ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
4 LOG all -- anywhere anywhere limit: avg 10/min burst 5 LOG level warning prefix "iptables INPUT dropped: "We want to add our new rule between #3 and #4 so that the last rule is always the LOG rule. We can do that by using insert with iptables, so that the new rule is inserted at position 4:
sudo iptables -I INPUT 4 -p tcp --dport 80 -j ACCEPTOnce that is done, we can list the rules to make sure they configured correctly:
sudo iptables -L --line-numberMy input chain has a new rule at the end:
paulh@ubuntu-server:~$ sudo iptables -L --line-number
Chain INPUT (policy DROP)
num target prot opt source destination
1 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh
2 ACCEPT all -- anywhere anywhere
3 ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
4 ACCEPT tcp -- anywhere anywhere tcp dpt:http
5 LOG all -- anywhere anywhere limit: avg 10/min burst 5 LOG level warning prefix "iptables INPUT dropped: "
Server Academy Members Only
Sorry, this lesson is only available to Server Academy Full Access members. Become a Full-Access Member now and you’ll get instant access to all of our courses.


